The invention redefines thread safe.
For comparison, two current definitions are shown below.
Due to blog incompatibility current version is located here.
Obsolete
Thread Safe Computers
Overview
Quote from Discover Magazine Jan 18, 2024
Ehrlich discovered that bacteria had different properties.
There were different types that he could identify and treat differently.
This led to antibiotics.
The computer also has different types of data.
Optimally, different types can be handled differently.
Program logic determines how data is used and software optimizes processing.
But hardware does not know how data is used, resulting in inefficiencies.
As a consequence, the hardware must use an algorithm different from the software.
Software is thread safe and minimizes the transfer of shared information.
Hardware is not and can not.
One inefficiency occurs in how computers synchronize their caches.
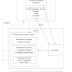
The synchronization is known as cache coherence. (Fig. 1 Current)
Another inefficiency is related to the memory bus which is controlled by the Bus Arbiter.
The bus arbiter is serial since it processes one request at a time.
The current algorithm shown in Fig.1 is simple.
Each time a processor stores a change in its cache,
the coherence unit must check all caches prior to changing main memory.
The cache coherence algorithm used by the hardware resolves integrity but is complicated.
Physical connections are required to synchronize hardware.
This complicates adding processors and memory buses.
The proposed thread safe computer is simpler. (Fig. 2 Proposed)
In contrast the current software thread safe algorithm reduces the amount of data requiring
synchronization to just one memory address (Fig. 3 Thread Safe). Memory is synchronized by
serializing control through one atomic swap instruction or mutex. The mutex is logical.
It is virtual.
The thread safe computer in Fig. 2 implements the current software thread safe memory logic.
The Bus Arbiter provides serialization and the mutex is executed in the memory controller.
The computer is thread safe.
This compares to the current mutex which is executed in each cache resulting in coherence.
This design requires an allocation instruction that enables hardware to differentiate
private data from shared data. This supplies the missing information that prevents the hardware
from being thread safe. The hardware needs to know whether data requires synchronization.
Benefits:
This new architecture extends the software's existing algorithm to the hardware making it thread safe.
This eliminates many hardware inefficiencies which duplicate function that the software already provides.
The entire coherence unit is duplicative and redundant.
In particular this design facilitates adding additional processors and memory buses.
It uses the existing software algorithm, so it can be applied to any multitasking computer system.
Current multiprocessors were designed before the mutex. They should be redesigned for the mutex.
Frank Yang
FrankYang43338 at acm dot org